Stop Phishing.
Protect Email Data.
Trust your inbox with Sophos Email security.
Prevent Phishing and Imposter Threats
Trust your inbox again with cloud email security protecting your people and critical information from malware, as well as malware free phishing and impersonation attempts.
Keep Imposters Out
Automatically identify your high-profile targets for malware-free impersonation and business email compromise attacks, then block the attack with machine learning analysis of message content.
Block Imposters
Criminals often impersonate key individuals in an organization or well-known brands to trick other employees into falling for their scams. With no malware or URLs to detect, Sophos Email uses advanced Natural Language Processing (NLP) machine learning to block these targeted impersonation and Business Email Compromise attacks.
NLP is a branch of artificial intelligence that focuses on helping computers to understand the way we humans write and speak. This enables Sophos Email to understand words in context rather than individually to extract notions like “urgency” and “asking for something” with an email and stop the message reaching your users.
For added protection, Sophos Email also includes a setup assistant that integrates with AD Sync to automatically identify the individuals within an organization who are most likely to be impersonated. It scans all inbound mail for display name variations associated with those users, further extending protection against phishing imposters.
Let Trusted Senders In
Authenticate all your senders without blocking legitimate email using SPF, DKIM, and DMARC authentication techniques and email header anomaly analysis.
Authenticate Senders
Adversaries are experts at using social engineering in their attacks. That’s why Sophos Email scans all inbound messages for key phishing indicators such as brand spoofing and impersonation attempts in real-time using SPF, DKIM, and DMARC authentication techniques and email header anomaly analysis. It spots and blocks phishing emails before they reach your users.
Stop Malware From Reaching the Inbox
Multi-layered protection utilizes over 35 years of threat intelligence, reputational and behavioral analysis, and state-of-the-art machine learning to eliminate malware and malicious URLs from reaching your inboxes.
Stop Malware
The danger with phishing is not the email itself but what it gets people to do. Phishing emails often include malicious links and malware attackers try to trick you into activating. Sophos Email Time-of-Click URL rewriting analyzes all URLs as they are clicked to block or warn users of risks, while the Sophos cloud sandbox accurately analyzes all files using multi-layered analysis and state-of-the art machine learning models. This ensures latest zero-day and unknown malware threats and PUA are blocked in minutes.
Protection Post-delivery
Automatically remove phishing emails containing newly infected URLs as soon as the threat state changes with continuous monitoring of Microsoft 365 mailboxes.
Post-delivery Protection
Email protection should continue to monitor messages once in the inbox. Safe URLs can be redirected to malicious ones, and malware can be inserted in previously safe sites. Sophos Email’s Search and Destroy API connection identifies these changes to threat levels automatically and removes malicious URLs, as well as the messages for Microsoft 365 users.
Messages identified by Search and Destroy can be viewed in your post-delivery quarantine summary.
Get Peace of Mind from Data Security
Secure sensitive data and make compliance easy. Sophos Email automatically scans messages and attachments for sensitive data, with encryption that integrates seamlessly.
Prevent Data Loss
Create multi-rule DLP policies for groups and individual users to ensure protection of sensitive information with discovery of financials, confidential contents, health information, and PII in all emails and attachments.
Encrypt and Authentication
Encrypt messages and add a digital signature to verify sender identity with S/MIME, or select from customizable encryption options including TLS encryption, attachment and message encryption (PDF and Office), or add-on full web portal encryption.

Increase Your Efficiency
Cybersecurity that works with your world
Sophos provides intuitive and incredibly broad visibility and protection, all managed from a single management console to increase efficiency.
- Say goodbye to email MX record redirections with Microsoft 365 API integration to get setup faster, and process messages sooner
- Empower your users with self-service controls to allow or block senders and manage quarantine
- Do more with your day, combining email protection with endpoint, server workload, mobile device security, firewall, zero trust, public cloud security in one console
Enjoy Faster Flowing, Safer Email
Sophos stops more threats faster, keeping email flowing to your users with high performance advanced threat detection and response.
Efficiency Built on Experience
Decades of threat intelligence data from SophosLabs means if we already know a message is bad, we block it at the source to optimize sandbox performance and deliver safe messages faster.
Blocking Bad Behavior
Threats constantly change their appearance. How threats behave is what remains constant. Sophos’ cloud sandbox analyzes all file processes, file activity, registry activity, and network connections to block ransomware and other forms of malware.
Power of Deep Learning AI
The same technology as our award-winning endpoint protection, Sophos deep learning artificial intelligence blocks zero-day malware and unwanted applications in their tracks.
Maximize Security Investments
With many cyberattacks starting with phishing. Sophos unlocks end-to-end visibility across your environments, with clear dashboards, detail threat reports, and extended detection and response.
Deeper Understanding of Threats
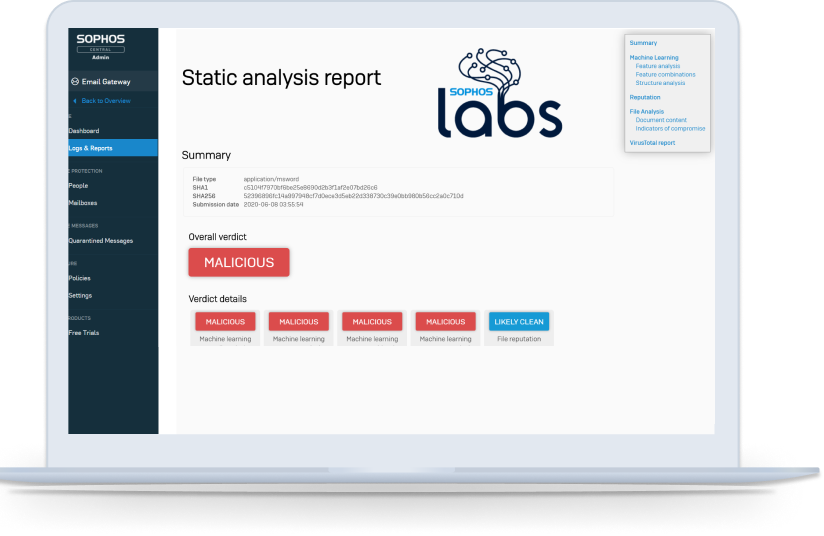
Anti-malware scanning and sandboxing provide detailed verdict reports based on machine learning analysis, file reputation, VirusTotal results and MITRE ATT&CK Matrix tactics to giving you a deeper understanding of threats targeting your organization.
Shared Threat Intelligence
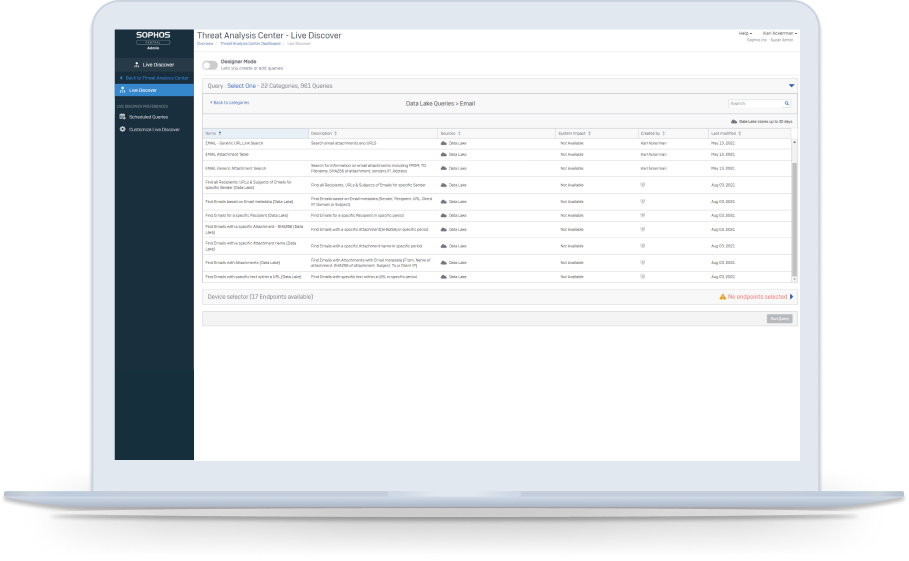
Maximize security investment with shared threat intelligence from endpoint and email protection in the Sophos XDR data lake. Enabling you to identify previously unseen indicators of compromise or and remove suspicious files across environments. Then extend visibility across Microsoft 365, cloud server workloads, the network and more.
Reduce Your Attack Surface
Sophos Email security is part of a broader Sophos ecosystem of protection, uniquely connected to automate threat detection and response.
Build Stronger Security Awareness
Cybersecurity awareness training is an important aspect of your security strategy. Sophos Email connects with Sophos Phish Threat, an additional service, to identify at risk users and increase security awareness through phishing simulations cybersecurity training modules.
Detect Compromised Mailboxes
Compromised devices lead to your brand and mailboxes being used to spread spam and phishing. Sophos Email security connects with Sophos Endpoint protection to automatically detect and stop these malicious messages.
Join a Security Partner Trusted by Thousands
Sophos is proud to support over 27,000 organizations with advanced email threat protection and data security. Compatible with all email services, including Google Workspaces Gmail, where you control the domain and DNS records, or through direct API integration with Microsoft 365 for even faster protection.
Modernize Cybersecurity Procurement
Sophos Email is now available alongside a range of other Sophos public cloud security solutions in AWS Marketplace. This helps streamline cloud security procurement, while counting towards any cloud provider consumption commitments your organization already has in place.
